During World War II, information was of utmost value. The allied powers needed to find an efficient and secure way to ensure that their strategic messages could not be intercepted and read by enemy forces.
In the Pacific campaign, Navajos serving in the United States Marine Corps addressed this issue through the use of cryptography. Essentially, they were able to encrypt messages using the Navajo language. In 1941, 29 Navajo soldiers became the original Navajo code talkers, tasked with rapidly and flawlessly translating English messages into the Navajo language. They then communicated the messages to each other in Navajo via radio, and finally translated the messages back into English.
The code called for English terms to be translated into words with similar meanings in Navajo. For instance, since there is no word for “battleship” in Navajo, it was literally translated to “whale”, which is “LO-TSO” in Navajo.
For uncommon English words, an encoded phonetic alphabet was created to enable translation one letter at a time. As the table below illustrates, letters were matched to words, which were then translated into Navajo. By the end of the war, the entire Navajo code included about 800 code words! Because the axis powers had no knowledge of the Navajo language, and due to the efficiency and accuracy of the Navajo code talkers, the allied powers were able to emerge victoriously.
The Importance of Encryption for Securing Information
As the Navajo code talkers illustrate, encryption is a vital tool in ensuring the security of information, whether it be on the battlefield or on the Internet.
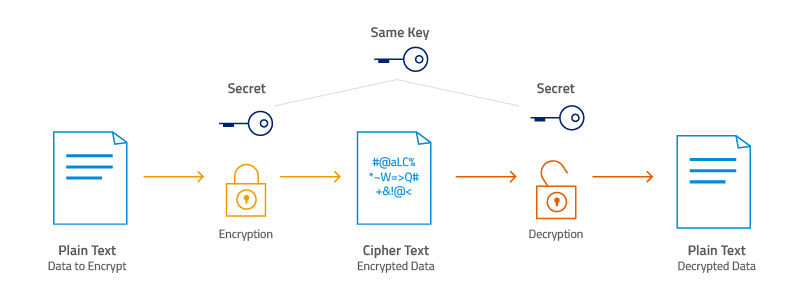
Encryption is, put simply, the process of scrambling information. It involves taking plain text (the original representation of the information—an image, program, or dataset—and converting it into an unintelligible, seemingly random ciphertext, which only authorized parties can then decipher.
The process of deciphering this information involves an encryption key, which is a string of values used within an encryption algorithm known only by the sender and receiver. In the case of the Navajo code talkers, English would be considered plain text and Navajo would be considered ciphertext. The encryption key would then be a shared knowledge of the Navajo language between the radio operators.

A Closer Look at Data Encryption and Why It’s Important
Although ciphertext may seem random to third parties, encryption follows a logical and mathematical algorithm so that a receiver with the key can decrypt encrypted data accurately and consistently.
Data can be encrypted both “at rest” (referring to data in storage) and “in transit” (referring to data transferred over networks). While it is possible for third parties without the key to decipher encrypted data, a secure, well-designed encryption scheme requires considerable time and resources to break. For a solid encryption scheme, brute-forcing (essentially guessing your way in) would take millions of years. The length of an encryption key is a general indicator of its strength; the larger it is, the stronger it is.
There are two main types of encryption:
- Symmetric Encryption: Symmetric encryption involves a single private key, which both the sender and the receiver use for encryption and decryption. Modern symmetric keys are usually 128 to 256 bits. Examples of well-known symmetric encryption algorithms include AES, Twofish, and Blowfish.
- Asymmetric Encryption: Also known as public-key encryption, asymmetric encryption involves one key for encryption and one key for decryption. This is also known as a key pair. These keys are large prime numbers with matching mathematical properties. The encryption key can be made public for everyone to use (hence the name “public key”), but only the receiver has access to the private decryption key to decipher the information. Modern asymmetric keys are usually 2048 bits. Examples of well-known asymmetric encryption algorithms include RSA and ECC.
Using Data Encryption to Stop Cyberattacks
In general, good key management involves changing keys often to maximize security. Encryption is of paramount importance in today’s digital world. Most, if not all, Internet users value privacy, security, and integrity in their online interactions and transactions. Encryption technology on the Internet is vital in preventing personal information—like bank account details or health information—from being leaked.
An example of a protocol that secures data sent between a web browser and a web server is HTTPS, which utilizes TLS protocol to keep information safe. Unfortunately, many organizations don’t value encryption and other cybersecurity practices as much as they should. According to a 2019 survey conducted by the French aerospace and security corporation Thales Group, less than 30 percent of enterprises encrypt data within their on-premises environments, cloud providers, or mobile devices. The security risks – and associated costs – are massive.
Of course, encryption alone isn’t enough to stop a powerful and well-planned cyberattack. Every day, hackers are developing new types of attacks to counter encryption – insider threats, attacks on encryption keys, ransomware, etc. This includes even the prospect of ultra-fast quantum computing calls for a major bolstering of modern encryption systems. However, it is undeniable that encryption is a fundamental pillar upholding the security of any platform. Combined with several other cybersecurity innovations and technologies, even the savviest of hackers are no match.
Keep Your Business Safe With Cybersecurity Expertise
Here at Golden Section, the security of your platform is of utmost significance. Too often, a new data breach brings another organization to its knees – a data breach that could have easily been prevented with appropriate encryption countermeasures. Like the ingenious Navajo code talkers, we are prepared to bring your industry victory with our cybersecurity expertise.