How Tech Companies Can Prevent a SolarWinds Level Breach
At the end of 2020, a Texas based Cybersecurity firm SolarWinds experienced a devastating breach in its software system. SolarWinds released compromised and faulty software patches to over 18,000 of its customers. While not all of the breached customers will be affected the same, the security impact and financial impact on many of the involved was severe.
While the exact date of the breach is unknown, this cyber espionage campaign, thought to be of Russian origin, can be traced back over a year. The hackers embedded malicious code into SolarWinds’ routine software updates, that when pushed to the public, almost every single customer using their service, Orion, would then be vulnerable to a hidden trojan horse.
The attackers had masked their presence within an array of systems and had been sitting quietly, stealing and observing data for many months. Luckily, an often-overlooked login security notification was flagged by a FireEye employee and FireEye, a California-based cybersecurity company, began an investigation into the report.
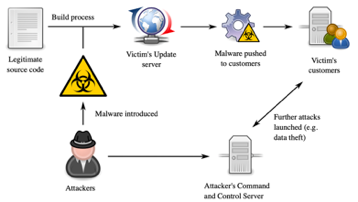
The leader of the FireEye’s investigation labelled the attackers as “one of the most advanced and disciplined hacking groups he had ever seen” as they used knowledge of security tools to intentionally avoid setting off security alarms or flags. FireEye claims that there is no way of addressing the size of the scope of damage that was done without further investigation.
SolarWinds’ software Orion has been implemented and utilized by more than 80% of Fortune 500 companies along with various government agencies. It took nine months for them to uncover that the attack occurred, but it will take much longer to uncover the further breaches and damages done to SolarWinds’ customers.
The most effective approach that could have been taken to limit the effect of the SolarWinds attack would be to make it as difficult as possible for any intruder to move laterally or vertically through the system. A zero-trust security architecture eliminates automatic trust from the organization’s network and tied in with privilege management makes a great defense to allowing an attacker get control over the complete network. At Golden Section Technology, we utilize Okta, an identity and access management tool, as our zero-trust defense to help manage secure sign-on and privilege policies.
At Golden Section Technology (GST), we believe in mitigating the risk of data breach before it happens, rather than dealing with the aftermath of a problematic “hack.” Investing in your company’s security defense practices lead to enhanced security protection for sensitive data, intellectual properties, as well as a lesser risk of loss due to breach. GST implements a variety of best security practices to ensure the protection of client software and the compliance with various security compliance protocols (PCI, GDPR, HIPAA Compliance, etc.).
Our development team maintains a current ISO 27001 certification (an international standard on how to manage information security) to ensure the trust of our clients in our development processes. At GST, we aim to safeguard client applications by implementing many best practices with application-level security, which refers to the security practices embedded within the software, such as data encryption, SQL injection protection, Cross-Site Scripting (XSS) protection, and more.
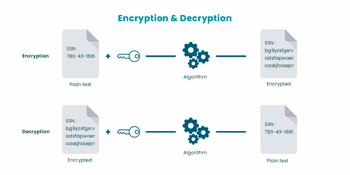
Data encryption is the process of transforming or encoding data before it's moved to storage. Data encryption allows confidential or proprietary information to be transferred over a secure channel. With the costs of data breaches being severely steep and the required notification of any breach, it is important to practice safer and secure storage techniques by using your own encryption. It’s also very important to ensure that all “data-in-motion” is encrypted while being transferred across networks. Since encrypted information is much more difficult to be deciphered, even if a breach does occur, a company using good decryption practices would not be required to notify users of the breach and could avoid many lawsuit and scandal nightmares like SolarWinds is currently facing.
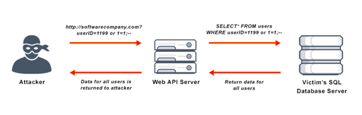
SQL injection is a common web-hacking technique that seeks to implant malicious code within a query field to grant unwanted access to sensitive information. To prevent this, many libraries offer methods of managing and parametrizing query inputs that ensure that only valid entries are accepted.
Cross-Site Scripting is a web security vulnerability that attackers can use to compromise interactions of users on the vulnerable application. These vulnerabilities allow attackers to control users’ actions and data. This poses larger issues if the hijacked user is granted high-level privileges that allow the attacker to gain full control of an application's functionality and data. As with SQL injections, XSS can be prevented by using a security encoding library.
However, even after performing all these security measures, a company may still remain weak against a cyberattack. This is because the weakest link of all in a company’s security, is the employee. The vast majority of hacks these days are not because a company failed to secure their application on the software side, but rather because an employee jeopardized access to sensitive information that could ultimately be used against the company in further exploitation.

Phishing is one of the most common methods of “hacking” a company. Using a fraudulent façade, hackers will attempt to steal information from employees in increasingly deceiving methods. Hackers will often pose as clients or other employees in hopes of gaining the trust of an unsuspecting individual. The best way to defend against this cyber risk is performing proactive training with employees during onboarding or annually. Employees should be aware of all forms of attacks they could be targeted be with and be ready to notify appropriate individuals when they find attacks.
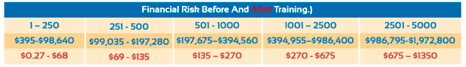
Since there are many vectors of entry that attackers may take to breach the cybersecurity of a company, it is the company’s obligation to have some form of defense implemented at every opening. Even if your software is impenetrable, you must ensure that your employee base is too. In the end, GST strongly believes in investing in your cybersecurity ahead of time, as it will be much cheaper and easier than trying to clean up the mess after falling victim to hackers.


